


Selection Experiments on Uniform Backgrounds
We conducted three successive runs of a selection experiment on our uniform fractal background (Bond & Kamil 2002), in which the effects of selection within experimental lines were contrasted to those in control lineages exposed to differing selective regimens (Kassen 2002). Each time, we began with the same parental population and continued predatory selection out to the 100th generation of progeny. Between runs, the jays were given 30 days of exposure to the parental population under stationary, non-evolving conditions to return them to a consistent baseline.
For each moth, we recorded whether it was detected by the jay and, if so, how long the bird took to find it. In addition, we estimated the resemblance of each moth to the background, using our crypticity index, and determined its phenotypic disparity from the rest of the prey population. To quantify disparity, we applied a non-parametric partitioning algorithm (Kaufman & Rousseeuw 1990) to the moth phenotypes in each generation, choosing a prototypical individual with minimal average distance from all others in phenotypic space. This "taxonomic distance" (Sneath & Sokal 1973) for each moth expressed the magnitude of its deviation from the prototype, and the average distance over all moths in each population provided an estimate of phenotypic variability.
To test whether observed changes in crypticity and phenotypic variance in the experimental lines were statistically meaningful, the results were contrasted with those from two sets of control lineages, one employing no selective agency and the other using frequency-independent directional selection based on parameters derived from global aspects of the jays' behavior. In both of the control treatments, we used the same population size, the same initial parental population, the same backgrounds, and the same mutation rate as in the experimental trials. In the non-selected lineages, however, the moths were never presented to jays, and the probability of being chosen to breed was uniform across the moth population, irrespective of phenotype. This provided a control for the occurrence of directional selection for crypticity in the experimental treatments.
The second control was designed to assess our primary hypothesis: that frequency-dependent selection resulting from hunting by searching image promotes increased phenotypic diversity. This required comparison to lineages in which selection was independent of the frequency of particular phenotypes, but was otherwise similar in intensity and direction to that produced in the experimental lines. For these control lineages, therefore, we determined the functional relationship between detection and crypticity for the jays, averaging over all of the results in the experimental lines. This function was then used to determine the probability of a moth's being chosen to breed.
The jays allocated their searching effort at least in part on the basis of the average degree of difficulty they experienced in finding the moths: Cryptic moths were detected more accurately and rapidly when the rest of the individuals in the population were cryptic than when the rest were relatively conspicuous. This "search rate" (Guilford & Dawkins 1987) or "caution" (Bond & Riley 1991) effect has been observed in other experimental studies of foraging behavior, and although caution cannot produce frequency-dependent predation when prey are presented in a randomized sequence (Endler 1991), it provides a solid basis for an alternative, frequency-independent control. The selection algorithm in the frequency-independent lineages was based on the empirical relationships between crypticity and detection performance in the experimental trials and fitted to the observed effects of mean population crypticity. We generated 200 selection lines of 100 successive generations using the non-selected and frequency-independent control treatments to provide controls for the selective effects of jay predation.
Crypticity Effects
Over successive generations, the experimental moths evolved to become significantly harder to detect, indicating strong directional selection for increased crypticity. The graphs below show changes in mean crypticity across successive generations in the three experimental lines (plotted with symbols), contrasted with the distribution of values from the two sets of control lines. Non-selected lines form the control group in panel a; the control in panel b was produced by frequency-independent selection. The graphs display medians (solid red) and 95% confidence limits (dotted) from 200 replicate control lines. Crypticity increased across generations to some degree in all three treatments; the increase was greatest for the frequency-independent controls and least for the non-selected lines.
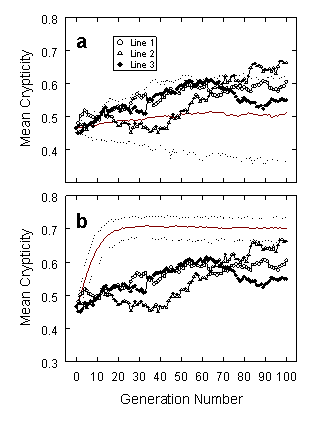
Selection in favor of individuals that resemble the background has been invoked as the probable cause of cryptic coloration in prey species for over a century (Poulton 1890), and there have been numerous demonstrations that predators preferentially feed on more conspicuous prey items (reviewed in Endler 1978, Cott 1957, Robinson 1969, and Diamond & Bond 2013). Our research is still, however, one of the only studies other than Endler's (1980) work on color-pattern selection in guppies that has shown significant directional selection by predators over multiple successive prey generations when compared to non-selected controls.
Phenotypic Variance
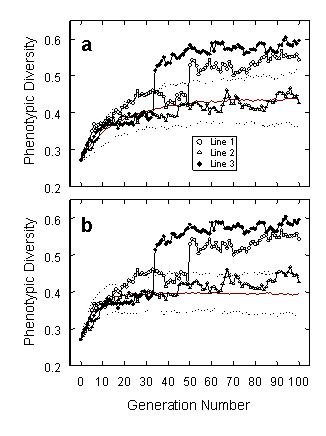
Our most important finding, however, was that the experimental lines showed significantly greater phenotypic variance than either control, demonstrating that frequency-dependent selection by visual predators can, of itself, promote high phenotypic diversity in prey species. The graphs below show changes in phenotypic variance of the digital moth population in the three experimental lines (plotted with symbols), contrasted with the distribution of values from the two sets of control lines. Again, non-selected lines form the control group in panel a, and frequency-independent lines are shown in panel b. Graphs display medians (solid red) and 95% confidence limits (dotted) from 200 replicate control lines. Phenotypic variance increased to some degree in all three treatments, but the increase was greater in the experimental lines than in either of the sets of controls. Experimental lines 1 and 3 each showed a striking, abrupt shift to a higher level of phenotypic variance at some point in the course of selection trials. In each case, the shift appeared to have been produced by the explosive spread of mutant regulatory genes affecting global levels of brightness or contrast.
Evidence for Searching Images
Additional analyses of the pattern of variation in detection as a function of prey sequences showed that the primary selective effect was due to jays overlooking atypical cryptic moths, the most elegant evidence of searching images that we have encountered and the first demonstration of searching images when the target stimuli were continuously variable.
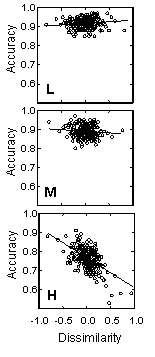 |
These graphs show detection accuracy on blocks of 100 trials as a function of crypticity of the target moth and dissimilarity between the target and the last previous correctly detected moth. Dissimilarity has been adjusted to remove the influence of mean phenotypic variance and mean population crypticity. Individual moth crypticity, c, increases from the top to the bottom panel: Low (c <= 0.45), Medium (0.45 < c <= 0.6), and High (c > 0.6). Regression lines indicate the relationship between accuracy and dissimilarity within crypticity levels. Note that dissimilarity has no effect on detection accuracy at low or medium crypticity levels. When the moths are very difficult to detect, however, the birds are strongly influenced by the sequence of prey encounters. When two similar, cryptic moths occur in sequence (low dissimilarity), the birds are much more accurate than one would expect; when the next moth is unlike the previous correct detection (high dissimilarity), however, the birds' performance declines, and they are much more likely to overlook the moth. This is precisely the pattern of responses that would be expected from hunting by searching image. |
References from Other Sources
Cott, H.B. (1957). Adaptive Coloration in Animals. London: Methuen.
Endler, J.A. (1978). A predator's view of animal color patterns. Evolutionary Biology 11: 319-364.
Endler, J.A. (1980). Natural selection and color patterns in Poecilia reticulata. Evolution 34: 76-91.
Endler, J.A. (1991). Interactions between predators and prey. In Behavioral Ecology, J.R. Krebs & N.B. Davies (eds.), pp. 169–96. London: Blackwell.
Guilford, T, & Dawkins, M.S. (1987). Search images not proven: A reappraisal of recent evidence. Animal Behaviour 35: 1838-1845.
Kassen, R. (2002). The experimental evolution of specialists, generalists, and the maintenance of diversity. Journal of Evolutionary Biology 15: 173-190.
Kaufman, L. & Rousseeuw, P.J. (1990). Finding Groups in Data. New York: Wiley.
Poulton, E.B. (1890). The Colours of Animals: Their Meaning and Use, Especially Considered in the Case of Insects. New York: Appleton.
Robinson, M.H. (1969). Defenses against visually hunting predators. Evolutionary Biology 3: 225-259.
Sneath, P.H.A. & Sokal, R.R. (1973). Numerical Taxonomy. San Francisco: Freeman.


